Agentic Workflows in the Enterprise: Open-Ended vs. Bounded Autonomy
A balanced evaluation of agentic architectures, comparing open-ended and bounded autonomy, and assessing their suitability for enterprise environments
12/3/20254 min read
Introduction
Organizations are exploring agentic workflows / orchestration as a way to make automated systems more adaptive, intelligent, and resilient. However, the term “agentic” is used to describe two very different architectural approaches, each with distinct implications for enterprise environments.
This article explains both models, examines their strengths and limitations, and evaluates their fit for enterprise operational systems.
Open-Ended Autonomy
Open-ended autonomy refers to systems where an AI model, typically an LLM, decides “what to do next” at runtime.
The system may still operate over a predefined set of allowed capabilities, but the selection of which capability to invoke, when, and in what sequence is delegated to the model
This results in a reasoning-driven control loop rather than a policy-driven one
Strengths
Adaptable to loosely defined or evolving tasks
Can flexibly reorder or combine actions
Reduces need for explicit procedural modeling upfront
Valuable for experimentation and discovery
Limitations
Stochastic behavior:
The same state can produce different next steps, even with the same menu of allowed actionsImplicit logic:
The decision policy is encoded in prompts and model weights, not in explicit rulesDifficult to audit:
Explaining “why a step was chosen” requires interpreting model internalsLow repeatability:
Model updates, prompt drift, or randomness change execution behavior over time
In short:
The problem is not the menu of actions;
it is the opacity and unpredictability of the logic used to select them.
Open-ended autonomy can excel in research, prototyping, or creative exploration—but introduces challenges for regulated, mission-critical environments.
Open-Ended Autonomy Flow
Bounded Autonomy
Bounded autonomy also operates over a finite set of approved capabilities, but the logic for selecting the next action is explicit, governed, and inspectable.
Decision-making is performed by:
Policy engines
Rules engines
Workflow orchestrators
State machines
LLMs, if present, act as advisors, not controllers.
Strengths
Predictable and reproducible outcomes
Traceable decision paths with auditability
Policy alignment and regulatory compliance
Lower operational and reputational risk
Operational stability with version control
Limitations
Lower creative flexibility
Requires capability and policy modeling upfront
In short:
The system adapts within constraints, rather than improvising beyond them.
This aligns more naturally with enterprise expectations for safety, control, and governance.
Comparative Analysis
A comparison across key enterprise criteria:
Both approaches involve capabilities.
The difference lies in who decides and how.
Enterprise Requirements
Enterprise systems operate under non-negotiable obligations:
Consistent outcomes
Explainable decisions
Implemented policies and controls
SLA performance guarantees
Risk containment and accountability
Regulatory compliance
Version stability and governance
Systems that cannot reproduce decisions or justify actions fail to meet these requirements.
This is not a maturity issue—it is a structural incompatibility.
Architecture Overview of Bounded Autonomy
Bounded autonomy is enabled through a layered architecture that separates governance, decision-making, execution, data, and integration.
The diagram below illustrates a high-level reference architecture that supports safe, adaptive workflows in enterprise environments.
At a high level, the system is composed of five execution layers, supported by a control plane:
1. Management & Observability UI (Control Plane)
This layer provides the interfaces to configure and monitor the system, including:
Policy & goals management
Agent and API registries
Operational dashboards and audit views
It ensures human oversight, transparency, and lifecycle governance.
2. Governance & Security Layer
Defines what the system is allowed to do, under what constraints, and for whom.
Key components:
Goals Catalog: business outcomes and SLAs
Policy Engine: decision rules and constraints
Guardrails: risk controls and safety boundaries
Access Control: roles, permissions, authorization
This layer enforces accountability, compliance, and safety.
3. Autonomy & Orchestration Layer
Executes workflows by selecting the next valid action based on policy and state.
Key Components:
Orchestrator: lifecycle and API entry point
Planner: selects actions under policy constraints
Router: exception and escalation pathways
Advisor: optional LLM reasoning for recommendations
Scheduler: retries, delays, timers, SLAs
This is where bounded autonomy actually happens.
4. Agents & Action Layer
Executes work through agents, APIs, and humans, sourced from registries.
Key Components:
Agent Registry: available internal agents and capabilities
API Registry: external tools and APIs
Human Reviewer: escalation, exception handling, approvals
This layer operationalizes action, integration, and human judgment.
5. Data & State Layer
Persists system state, policies, and audit history to support accountability and replayability.
Core stores:
Goal Store
Policy Store
Process Store
Audit Log and Telemetry
This layer ensures traceability, reliability, and learning over time.
6. External Integration
Provides safe connectivity to enterprise systems and external services using:
API gateway
Message queues
Event bus
This allows the system to operate within existing enterprise ecosystems.
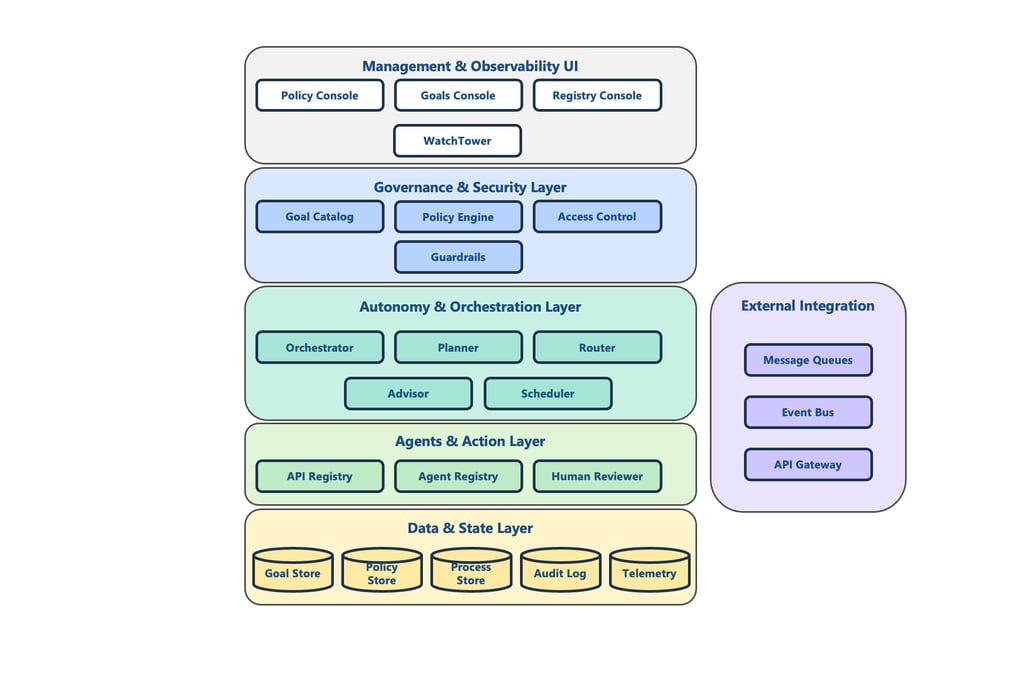
Architecture for Bounded Autonomy
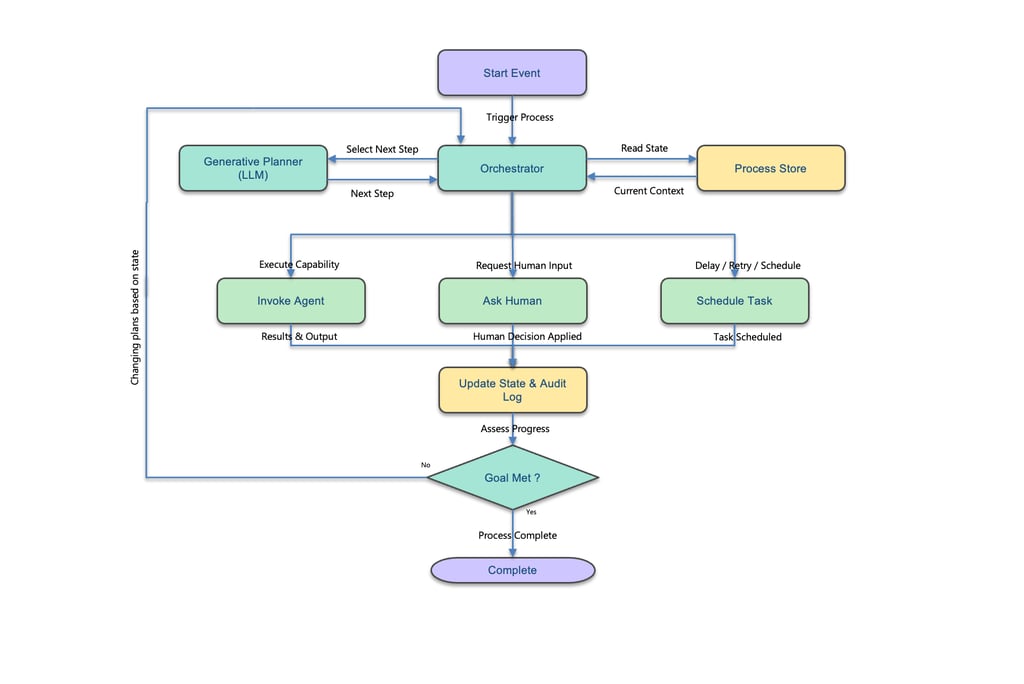
Execution Loop in Practice
Operational agentic workflows follow a closed-loop decision cycle that balances autonomy with control. At each iteration, the system:
Receives a trigger that initiates or continues a process
Evaluates current state from the process store
Consults policies and constraints to understand allowable actions
Selects the next valid step under policy and SLA boundaries
Executes the step through:
an automated agent
a human decision
or a scheduled task
Updates state, audit, and telemetry based on the outcome
Assesses progress toward the goal or SLA
Loops back to the planner if more work is required, or completes the process if satisfied
Unlike static workflows, this loop is dynamic and state-driven—the next action is chosen based on context, policy, and outcomes, rather than a hard-coded sequence.
Autonomy exists, but it operates within explicit governance boundaries, not improvisation.
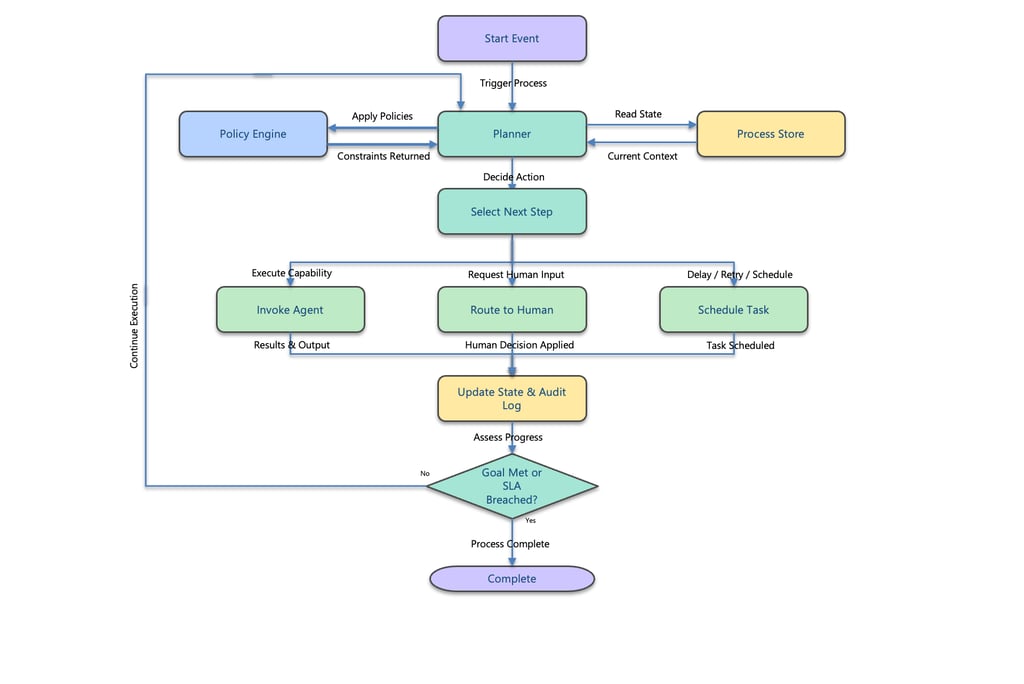
Execution Flow - Bounded Autonomy
Where Each Approach Fits
Open-ended autonomy is best suited for:
Research and experimentation
Creative ideation and prototyping
Exploration of novel patterns
Systems where variability is acceptable
Bounded autonomy is suited for:
Operational workflows
Regulated environments
Financial and compliance-sensitive systems
Mission-critical processes
Because enterprise systems carry legal, financial, and reputational obligations, they need architectures that guarantee safety, accountability, and repeatability.
Conclusion
Agentic workflows represent a meaningful evolution in automation, but architectural choices must reflect operational realities.
Open-ended autonomy can be powerful in exploratory settings, but its stochastic, implicit decision logic is difficult to reconcile with enterprise requirements for determinism, auditability, and governance.
Bounded autonomy offers a pragmatic foundation for agentic systems that are:
Adaptive
Accountable
Compliant
Repeatable
Operationally safe
A useful way to summarize the distinction is:
Enterprise autonomy is not about maximizing freedom—it is about ensuring responsible, governed performance.
For organizations adopting agentic systems, bounded autonomy provides a path to intelligent automation that enhances capability without compromising control.